The shorter story:
We published the original Darknet paper in 2001. The paper initially caused a huge stir in a few very small places, which Timothy B. Lee captures well in this excellent article.
Everybody is suddenly freaking out about 3D printed guns, so I just updated our original paper to make the 3D gun and darknet connection more clear: The Darkweb and the Future of Gun Control.
The longer story:
Back in 2001 I started thinking about what’s next for the Darknet, and 3D printed guns looked pretty obvious to me. I talked about this, wrote about it and generally sounded the alarm for the following decade (recall that this was WAY BACK in the early 2000s so there weren’t that many places to sound an alarm, and even fewer people who cared).
In 2013, 3D printed guns were finally “here”: First via Cody Wilson’s near-deathtrap of a .380 which he (bravely) made using consumer-grade 3D printing, and then later in the year in a much safer, more powerful and far more expensive all-metal 1911.
After doing the Darknet and the Future of Everything talk for Gov 2.0, I said I was done talking about it. You can’t roll your eyes at me anymore! Ha! SO THERE! ALL DONE!
However very recently there’s been a broad public freak out over 3D printed guns. It’s been 5 years since I said I was *done* talking about this stuff and now half of the news stories I am hearing are all about it. So I guess maybe I’m really not done after all.
Here’s why I think this story is mostly about the darknet, and not 3D printing nor guns:
In 2013 Wilson immediately put the files for his gun on the internet where they were downloaded 100K times before being taken down. However those files have clearly been “darknetted” as they have been showing up in different parts of the internet ever since.
What about the 1911 pistol files? There are many copies of 1911 design files on the internet. The underlying technical drawings used to build those files have been in the public domain for nearly 100 years and are all over the place. For nearly a century, those drawings haven’t been usable by anyone except skilled machinists, so they were “safe” (kind of like how locks used to be safe).
The drawing below shows the exact dimensions and tolerances – everything actually needed – to make what the US legally calls an actual firearm. There are about 50 parts in a 1911 pistol, but only one of them is legally a gun, and that’s the receiver, which is drawn below. Note that the date of the file is 1936.
Can I take this drawing and feed it into a 3D printer? Of course not… yet. Not YET. 3D printers *currently* need data described to them in very specific ways. However it’s extremely easy to assume that within 10 years (perhaps less than 5) we will be able to take this exact photo and print out the resulting “gun”, because that’s how technology works. It keeps getting better. 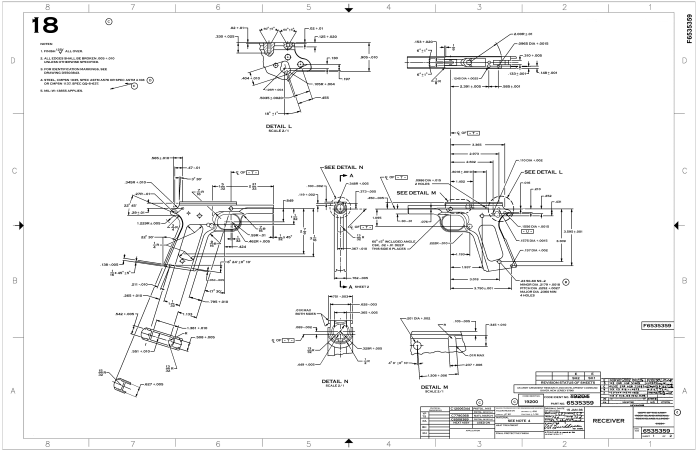
Seventeen years ago we showed, in a peer-reviewed scientific paper that has withstood rigorous and ongoing investigation and citation, that you can’t effectively control the distribution of desirable data. 3D printable gun files are clearly going to be desirable enough to be subject to being darknetted. Any responses or reactions to this fact must take this into account.
Excerpt from The Darkweb and the Future of Gun Control:
ANY PHYSICAL OBJECT THAT CAN BE REPRESENTED AND DISTRIBUTED AS DIGITAL DATA SHOULD BE CONSIDERED A FULL BENEFICIARY OF THE CONCLUSIONS OF THIS PAPER. 3D PRINTED GUNS START OUT AS DATA. They are then rendered (which is to say, made usable in the analog universe) in a 3D printer. They are no different from music, books or movies. If you want to freak out about things that still haven’t quite happened yet imagine the future of CRISPR and drug recombination, which is also just digital information that is rendered through a “printer”. Add nano-explosives, autonomous drones, diseases, bacteria, viruses, DNA, “fake news” and porn face swapping. Anything that can be data will be darknetted.